Phishing Protection
Phishing (= password fishing) is a common form of attacks on computer users. The attackers fake emails and websites of legitimate companies and organizations. The attackers use this as an excuse to persuade users to enter sensitive information, usually access data such as passwords or PINs.
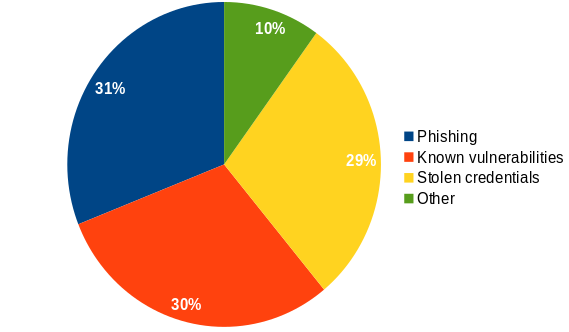
Weak or stolen passwords as well as phishing are among the most common gateways for successful hacker attacks, at around 60%, as an IBM study from 2019 shows.
FIDO U2F and FIDO2
With FIDO U2F and FIDO2 or WebAuthn, there are new standards that enable robust two-factor authentication (FIDO U2F) and passwordless login (FIDO2).
For two-factor authentication (2FA), all you need is your Nitrokey FIDO U2F or Nitrokey FIDO2 and you trigger the 2FA at the touch of a button on the Nitrokey.
For the password-free login (FIDO2 or WebAuthn), you only need your Nitrokey and can use it to log in to e.g. Microsoft services (Windows, Office 365) and other web and enterprise systems (e.g. Nextcloud) at the touch of a button and by entering your PIN, without any password (if desired, even without a user name).
Both methods (FIDO U2F and FIDO2) offer high security. Thus the Nitrokey checks whether the domain used actually belongs to the service. This makes phishing attacks on a technical level much more difficult.
Advantages
- Simple usability at the touch of a button (and device PIN if necessary).
- High security against phishing attacks (through integrated domain check).
- More secure than other two-factor authentication methods (e.g. SMS or TOTP/HOTP).
- By supporting all common web browsers, no additional client software or driver installation is necessary.